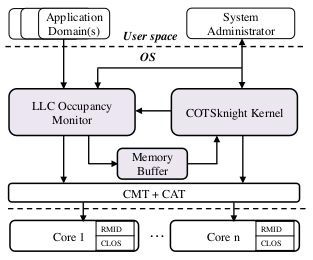
Researchers at GW are developing COTSKnight, a novel framework that offers a holistic infrastructure for both detecting and defending against cache-based timing channels. Cache timing channels endangered shared computer system by stealing information without leaving physical traces in shared cache. COTSKnight repurposes the performance monitoring tool and detect various protocols of cache timing channel with no false negative and zero hardware modification.
Cloud Platform would become a 150-billion-dollar market by 2022. 41% of the cloud platforms are public platforms where user’s workload would be running with applications from strangers on the same physical machines. People are deploying various types of workload on public cloud including sensitive ones. 58% of cloud usage is consumed by developing operations of companies. 20% of cloud usage is related to research experiments. Those sensitive applications contain critical information from industry and academia. However, as demonstrated by prior research, cache side channel is able to infer the secret from running applications on shared platform. Different from traditional computer virus, the cache side channel is based on shared architecture which cannot be tracked by security software.
Investigations show that the security of public cloud become the biggest concern of customers. COTSKnight is designed to solve the biggest concern of a future 150 billion market. Comparing to prior proposed solution, COTSKnight does not require hardware update which would cost extremely high for cloud service provider. COTSKnight repurposes the hardware performance monitoring tool to observe cache occupancy change for processes. Advanced signal processing techniques are applied to the observation result and the suspicious applications would be identified. The suspicious applications would be assigned to separated cache ways to disband the information leakage through cache side channel. Experiment on real system shows that our mechanism can stop all cache side channel with less than 4% overhead.
Applications:
1. Cloud platform operators including Amazon, Google, IBM and Microsoft
2. Personal computer systems that run workloads from multiple potential untrusted source
Advantages:
1. COTSKnight can be deployed to commercial-off-the-shelf computer system while prior secured cache design require user to replace all existing hardware infrastructure.
2. COTSKnight can detect all demonstrated cache timing channel in noisy background.
3. COTSKnight induces less than 4% overhead for benign workloads. In some scenarios, the COTSKnight can improve the performance of applications because it stops cache conflicts.